I am done with the first two parts of this highly requested YouTube video series! Check out the first two parts here:
Category Archives: Microsoft Windows Server
User Account Control (UAC) in Windows 10
This post serves as a supplement to my MD-100 training at CBT Nuggets! Enjoy!
I remember a friend at CBT Nuggets telling me quite boldly – “Windows was ruined for me when UAC hit!”
My guess is, it was probably around the poorly received Windows Vista when my friend formulated this opinion. Suddenly for him, Windows would interrupt his workflow with noise, some visual fanfare, and a question if he was really sure he wanted to do what he was trying to do.
In fairness to Microsoft, other Operating Systems take a similar approach – and this is a key element to truly securing the client.
Regardless of what you think about UAC, this post is meant to ensure that you completely understand it and that you can completely control it! For those of you studying Windows Server 2016 (or later), please understand that this post also applies!
Microsoft’s UAC helps prevent malware from damaging a PC. With UAC, apps and tasks always run in the security context of a non-administrator account, unless an administrator specifically authorizes administrator-level access to the system. Because of this security context, UAC can block the automatic installation of unauthorized apps and prevent inadvertent changes to system settings.
UAC allows all users to log on to their computers using a standard user account. Processes launched using a standard user token may perform tasks using access rights granted to a standard user. For instance, Windows Explorer automatically inherits standard user level permissions. Additionally, any apps that are started using Windows Explorer (for example, by double-clicking a shortcut) also run with the standard set of user permissions. Many apps, including those that are included with the operating system itself, are designed to work properly in this way.
Other apps, especially those that were not specifically designed with security settings in mind, often require additional permissions to run successfully. These types of apps are referred to as legacy apps. Additionally, actions such as installing new software and making configuration changes to the Windows Firewall, require more permissions than what is available to a standard user account.
When an app needs to run with more than standard user rights, UAC can restore additional user groups to the token. This enables the user to have explicit control of apps that are making system-level changes to their computer or device.
But what about controlling the interruptions of your workflow? Well, the amount of “permissions granting” you must do is configurable with four basic levels. Keep in mind you can also make changes to UAC with various Group Policy settings that exist.
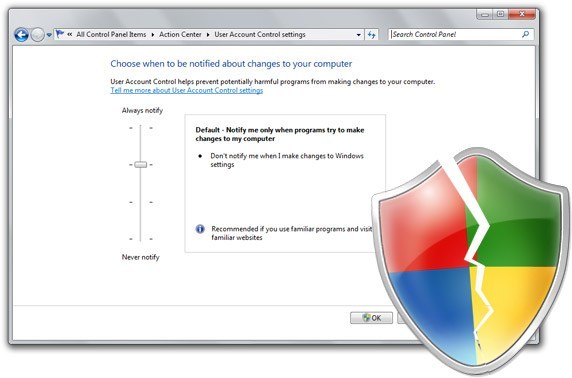
Here are the four levels of control that we should know. To set the level is easy, just search for UAC and click the option to change the UAC settings.
UAC has a slider to select from four levels of notification:
- Always notify will:
- Notify you when programs try to install software or make changes to your computer.
- Notify you when you make changes to Windows settings.
- Freeze other tasks until you respond.
Recommended if you often install new software or visit unfamiliar websites.
- Notify me only when programs try to make changes to my computer will:
- Notify you when programs try to install software or make changes to your computer.
- Not notify you when you make changes to Windows settings.
- Freeze other tasks until you respond.
Recommended if you do not often install apps or visit unfamiliar websites.
- Notify me only when programs try to make changes to my computer (do not dim my desktop) will:
- Notify you when programs try to install software or make changes to your computer.
- Not notify you when you make changes to Windows settings.
- Not freeze other tasks until you respond.
Not recommended. Choose this only if it takes a long time to dim the desktop on your computer.
- Never notify (Disable UAC prompts) will:
- Not notify you when programs try to install software or make changes to your computer.
- Not notify you when you make changes to Windows settings.
- Not freeze other tasks until you respond.
Not recommended due to security concerns.
So, it is worth noting, an expert user that knows how to avoid invalid Web sites and bogus applications can never be bothered with UAC alerts and confirimations. But please note, they better be truly expert at avoiding such potential problems!
For more information on the new Windows 10 exams – check out: